SurfSolo | Private Internet Browsing System
Powerful software that allows the user to get totally anonymous and at the same time protects the data exchange on the Internet.
**FREE DOWNLOAD (v2.0)**
File Size: 1.4MB | Safe & Verified
Security And Privacy
Network Security
Shareware
Key Features
- No one knows more about “surfing†and downloading habits than your ISP (Internet Service Provider).
- The ISP is able to know who you are, every site you visit, every page you view, and every file you download.How this happens?Every time you are connected on the Internet your ISP gives you an IP number that is a unique address which identifies you from the other computers on the network living you vunerable to any attacks from hackers or eavesdroppers.SurfSolo was created to protect you from those problems.Powerful software that allows the user to get totally anonymous and at the same time protects the data exchange on the Internet.The software provides a direct encrypted link(by using SSH Protocol) with one of the world wide SecurStar high bandwidth security proxy servers.“SSH protocol (Secure Shell protocol)†which makes the connection encrypted from your personal computer to any website.
- A protocol says which format the data is going to be sent and which rules will be applied.
- The SSH protocol creates a “virtual tunnelâ€, in such a way you are totally invisible from any kind of monitoring.
- If someone tries to track your IP number, it will recognize only our SecurStar server\'s IP, so it would be impossible to track your personal IP number.The SurfSolo also provides free e-mail account (no mailbox size limit).
- Sending emails from it will not reveal your personal IP number.At the moment SecurStar has 5 proxy servers available around the world (Malaysia, Hong Kong, Germany, Holland and Czech Republic).When the customer purchases the software he can choose one of the Proxy servers available.
Technical Specifications
- Publisher: Securstar.com
- License: Shareware
- Operating System: Windows 7, Windows 8, Windows 10, Windows 11
- Category: Security And Privacy / Network Security
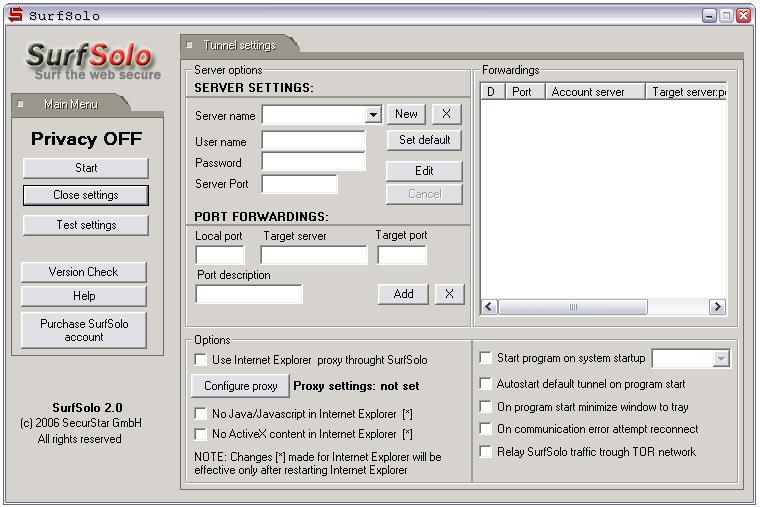
Screenshot
User Rating
Based on 252 reviews.